Blockchains were built for transactions. Products need more.
Today’s blockchains are optimized for execution, not long-lived products.
They order and secure data reliably, but they were never designed to support complete, evolving applications over many years.
As real users, regulation, and scale come into play, architectural limits begin to surface.
The business limitation
- Applications are tied to global, inflexible execution rules
- User experience depends on off-chain infrastructure
- Compliance and auditability stop at the backend
Why this matters. For real products and organizations, this means:
- Higher operational risk
- Fragmented system architecture
- Limited ability to evolve or specialize
What works for experimentation does not work for production.
To support real-world applications, blockchain infrastructure must become modular by design.
Execution must adapt to business needs, not the other way around.
The LEA Breakthrough
A modular blockchain built for real applications.
LEA is designed from the ground up to support applications as products, not just transactions as events.
Instead of forcing every use case into a single execution model, LEA introduces a modular architecture that adapts to different application needs.
What makes LEA different
- Modular execution instead of monolithic chains
- Independent execution domains (PODs)
- Applications evolve without global protocol changes
- Backend logic and user interaction become part of one system
The result
A new class of decentralized applications:
- Complete
- Verifiable
- Built to last
The Four Pillars of LEA
Four principles. One application platform.
LEA brings together four foundational principles that, combined, enable a new class of decentralized applications. Individually, they exist elsewhere. Together, they don’t.
Modular Execution
Applications should adapt to their domain, not the other way around.
LEA separates consensus from execution, enabling independent execution domains that evolve without global protocol changes.
Verifiable Applications
What users see must be as trustworthy as what the application does.
LEA makes it possible to verify not only execution logic, but also application interaction, closing the trust gap between backend and frontend.
Post-Quantum Security
Security that is built for the future, not retrofitted later.
Post-quantum cryptography is integrated from the start, ensuring long-term resilience as cryptographic standards evolve.
Compliance-first Design
Infrastructure that works beyond experimentation.
LEA is designed to support regulated and non-regulated long-lived applications, with clear boundaries, auditability, and adaptability built into the system.
Built step by step. With production in mind.
What Exists Today
LEA is not a concept. It is an evolving blockchain platform, developed deliberately and transparently. We prioritize correctness, security, and long-term viability over rushed launches.
What is live today
- A functional LEA network running in a controlled, single-node environment
- Transactions secured with post-quantum cryptography
- A live Web3 SDK used to submit and process LEA transactions
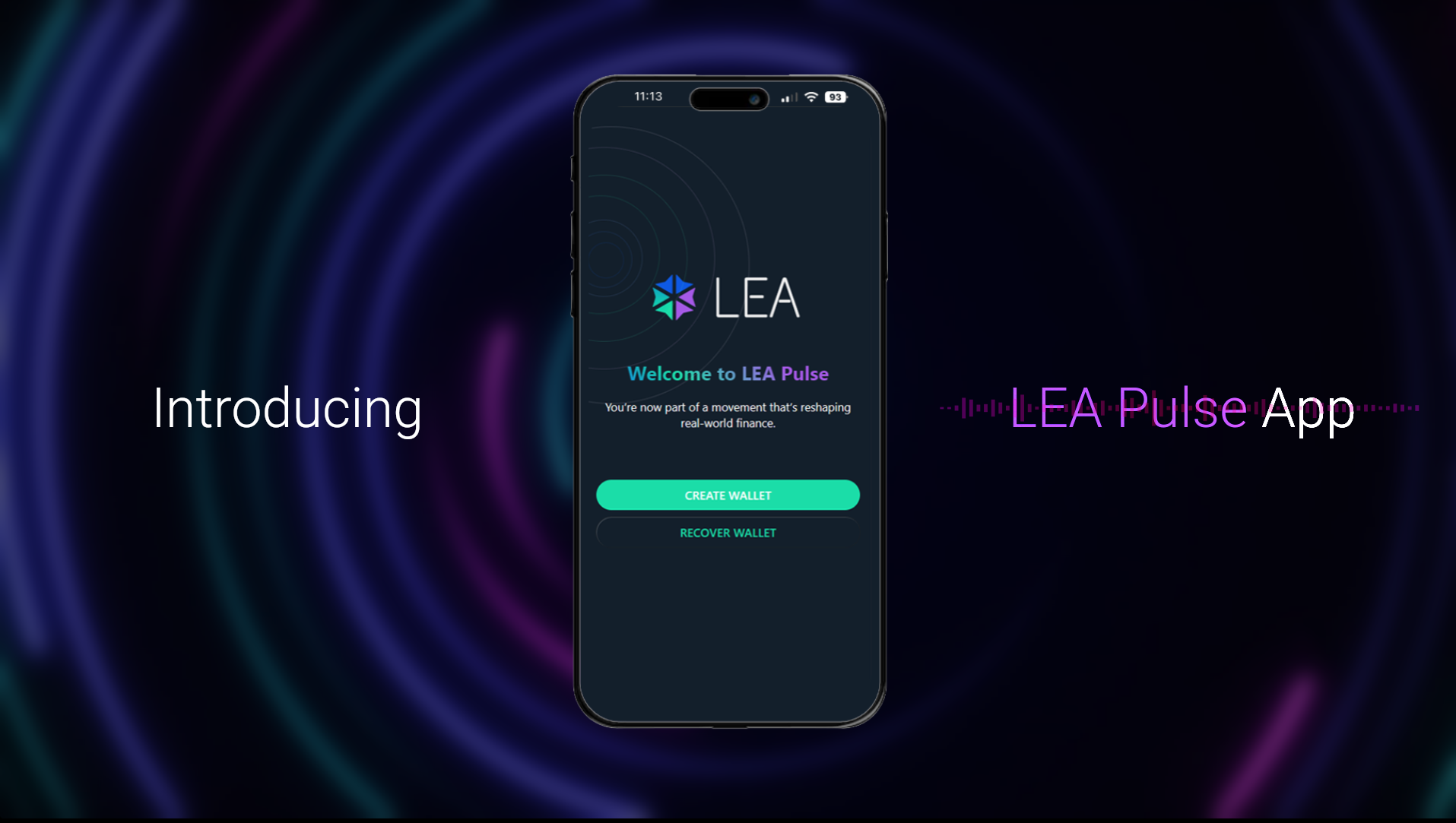
- LEA Pulse, the official mobile app for onboarding, wallets, and community participation
What is currently in development
- The on-chain execution MVP for fully on-chain applications
- The decentralized consensus layer
- Expanded developer tooling and domain-specific execution environments
Articles and Information to stay informed
Latest News
2025 in Review: Building the Foundations of LEA
December 23, 2025
As the year ends, we want to reflect on our progress at LEA and our future direction. LEA focuses…
0 Comments4 Minutes
Modular Blockchain Architecture: Quantum-Resistant Security for the Future of Web3
September 10, 2025
Blockchain faces a quantum threat. LEA’s modular architecture turns this challenge into an…
0 Comments6 Minutes
LEA Pulse (Alpha): Your Starting Point in the LEA Ecosystem
May 13, 2025
LEA Pulse alpha onboarding app is your early access point into the LEA Blockchain ecosystem. Built…
0 Comments4 Minutes
Unlocking Efficient Data Encoding with LEA: Inside the Serialization Codecs Project [Tech]
April 25, 2025
LEA blockchain serialization codecs are powering the next generation of data encoding for…
0 Comments5 Minutes
Suite25519 Cryptographic Library for Real-World Assets | LEA Blockchain [Tech]
April 24, 2025
Suite25519 is a modern cryptographic library built for real-world assets — secure, lightweight, and…
0 Comments5 Minutes
Got Questions? We’ve Got Answers.
FAQ.
LEA is a modular Layer 1 blockchain built for maximum developer freedom.
It separates consensus from execution, so you can launch your own application-specific environments (PODs) with custom logic, cryptography, and governance without protocol changes.
A POD (Programmable Object Domain) is a self-contained execution environment on LEA.
Each POD can define its own rules, signature schemes, tokens, and permission systems. It’s like launching your own mini blockchain on top of a shared, secure ordering layer.
The BasePOD is LEA’s first and foundational Decoder—where all PODs register and cryptographic standards originate.
It provides the base registry for new PODs and implements Post-Quantum Cryptography by default. Other PODs can build on this or define their own cryptographic logic as needed.
No, but they must register with the BasePOD.
Launching a POD is permissionless, but to become discoverable and interoperable within the LEA network, your Decoder must register through the BasePOD registry.
LEA Pulse is our official community app—your access point to the LEA ecosystem.
-
Create a secure, non-custodial LEA Wallet
-
Earn $LEA through early engagement and XP tasks
-
Stay informed via Founder’s Voice direct updates
-
Prepare for DAO governance participation
It’s not for developers—it’s for users, contributors, and early supporters.
Yes.
While the BasePOD uses quantum-secure schemes like SPHINCS+, each POD can implement its own cryptographic logic. You’re free to use Ed25519, Dilithium, or even experimental ZK signatures—whatever fits your threat model.
Yes, by design.
The BasePOD uses post-quantum signature schemes like FALCON-512 for core identity and transaction verification. Other PODs can use the same or bring their own cryptographic frameworks.
Pre-Register for Early Access to the LEA Ecosystem
Join Early. Build Together.
Be one of the first to explore the LEA Pulse app — your gateway to wallet creation, quests, and community engagement. Early adopters get access to tools, tasks, and updates that help shape the future of our blockchain.